Data Center Specifications
The AXIS Cloud Infrastructure is powered by eFolder-owned equipment co-located in large-scale, secure, enterprise-grade data centers in Atlanta, Salt Lake City, Kelowna (B.C., Canada), and Amsterdam (Netherlands). These facilities are designed for 99.999% reliability (no more than 5 minutes average downtime per year), are SSAE 16 Type II Certified (replacement for SAS 70 Type II), and are HIPAA and PCI Compliant. While specifications of each facility vary slightly, all are designed to be highly secure and fault tolerant. For example, our Atlanta facility features the following:
Security
- 10 foot razor fence with 24/7/365 surveillance and patrols by armed security guards.
- State of the art data center ID system and security including video surveillance and recording.
- Multi-level identity verification, including biometric scanning, card keys, and badge authentication.
- Real-time IPS and multilevel firewalls that comprehensively autoblock sources of rejected traffic.
Power (2N+1)
- Multiple utility feeds from separate substations with diverse building entry
- 11 generators providing a total of 7 MW of power, with in-ground fuel tanks to provide uninterrupted power for several days of outages. Fuel contracts guard against long-term outages.
- A+B feeds to each cabinet with A+B computing equipment, with each feed backed by independent N+1 power paths, including breakers, UPS systems, generators, and main feeds.
- A connection to the most reliable power grid in the state of Georgia through quad vaults on 4 feeds. This grid protects the main hospital in Atlanta so it is on a last outage program for critical services and was extensively upgraded for the Olympics. For the last 8 years the generators have only been used for testing.
Environmental Controls (N+1)
- Environmentally friendly chilled water cooling, fed by redundant water sources (private well, city main), and powered by redundant pumps and paralleled 500-ton cooling towers.
- Redundant Liebert Air systems providing consistent temperature and humidity range throughout the 70,000 square feet of datacenter space.
- Continual environmental monitoring in each cabinet and through the data center, with threshold alarms monitored by the 24/7/365 NOC, providing fast resolution of anomalous conditions.
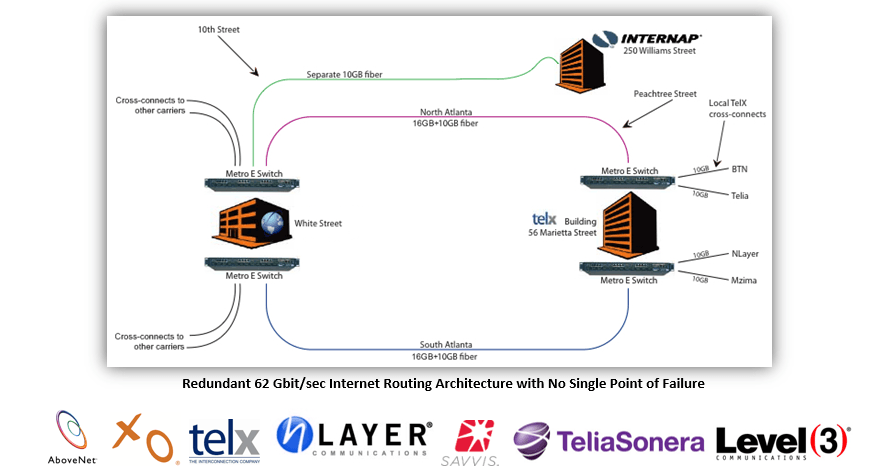
Network (2N)
- Redundant Cisco BGP routing and switching infrastructure with cold spares on site. If equipment failure occurs, there is no interruption of service.
- 62 Gbit/sec Internet connectivity, delivered through multiple independent fiber rings and lines. Dual feeds of all aggregation routers ensure 100% uptime - some of the best in the business.
- Avaya ANS BGP4 management system optimizing the routes on the network in real time, 7000 times per minute based upon trace route performance, to ensure low latency and high throughput.
- 6 backbone providers who are publicly peered with 12 providers including Earthlink. Our current network consists of multiple 10 Gig or Gig links to Abovenet, Cogent, Level 3, nLayer, SAVVIS, TeliaSonera, XO, and the Atlanta Internet Exchange public peering point.
Data Integrity and Security
When dealing with millions of GBs of data (petabytes), the utmost care must be taken to ensure that customer data is protected and preserved by adhering to the highest standards of data security and by providing systems that guarantee the integrity of the data. Although many cloud service providers talk a lot about data encryption, most don’t discuss or provide mechanisms to guarantee the integrity of the data, which is equally as important. After all, what good is your data if it becomes corrupted or damaged?
Silent data corruption is a real threat to your data. In a recent study by CERN, silent data corruption was observed in 1 out of every 1500 files. Redundant storage, RAID, mirroring, checksums on individual components, replication, and even backup are not sufficient to protect against silent data corruption. If data is silently corrupted without detection, this corrupted data is then replicated or backed up, thereby corrupting any redundant or backup copies. The causes of silent data corruption are many and include hardware, firmware, and software faults.
Our data integrity protection systems are second to none. Our end-to-end 256-bit checksums “tag” your data with cryptographically verifiable identifiers, and these checksums are then used to verify the integrity of the data throughout the entire process. If corruption within a particular block is detected, a redundant copy of that block is used to automatically repair the corruption.
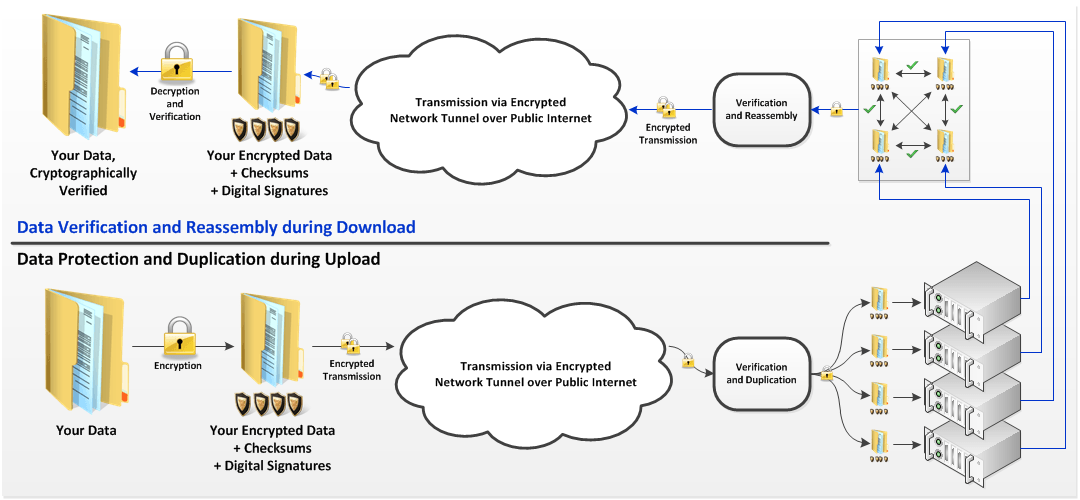
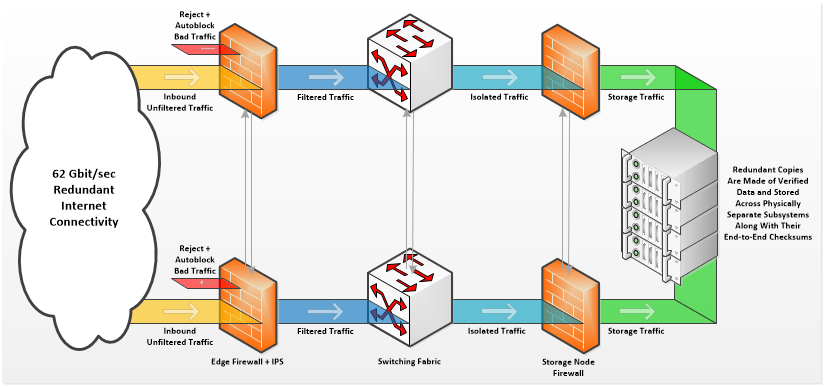
The redundant copies of the data are split across physically separate raw storage devices each located in physically distinct storage subsystems. Storing the redundant copies physically far away from each other ensures that clusters of disk failures due to localized vibration, enclosure failures, or IO controller failures do not affect more than one redundant copy of the data, providing an unparalleled level of protection.
In addition to automatic detection and repair upon data access, all data is periodically verified against their end-to-end checksums to proactively identify and automatically repair silent data corruption.
As an additional measure of data integrity assurance, every data block backed up to our cloud is digitally signed by your encryption key and then verified during restore. This provides cryptographic assurance that your data has not been tampered with by anyone and is 100% identical to what was originally backed up.
We’re also serious about data confidentiality. In addition to our in-depth network security mechanisms, our services adhere to stringent internationally accepted standards for data encryption and network transmission, including AES 256-bit, FIPS-197, NIST 800-38A, HMAC-SHA-256, PBKDF2, and RSA 3072-bit.
Secure, Always-on Network
High performance and resilient internet connectivity is crucial to providing fast and reliable cloud services. Our network connectivity has unparalleled redundancy and performance, utilizing geographically diverse external fiber paths, distinct fiber entrances, mesh routing, and extensive peering relationships. Actual measured uptime over the past 5 years exceeds 99.998%–even if scheduled maintenance periods are included in the uptime measurements. The network has truly proven itself to be an always-on network.
Security is equally important at every layer and participant in the network. Real-time security ensures threats are stopped cold. Attempted network probing or rejected packets cause senders to be immediately blocked. Separate and independent firewalls dedicated to each storage node combined with security filters inside the switching fabric provide deeper isolation, segmentation, and threat identification and mitigation.
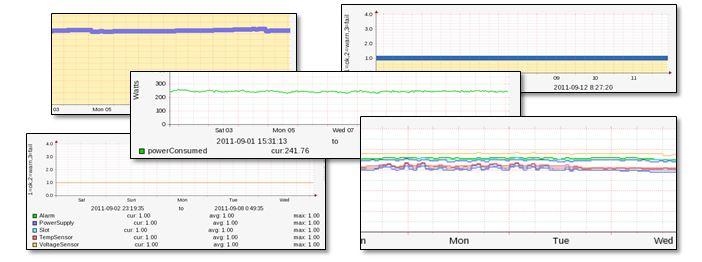
Monitoring and Management
Real-time monitoring of all networks, servers, services, storage, and other key IT infrastructure is critical to providing reliable cloud services you can depend upon. We use two separate external and an internal automated monitoring systems, which leverage differing technologies to monitor the same systems. This diversity of monitoring technologies and systems ensures that our engineers will always be alerted of degradations in fault tolerance or performance. Alerts are processed 24/7/365 by our team of engineers.
We operate true “lights-out” data centers. Once new equipment is physically installed, our engineering team has comprehensive control over every component in the data center. Except for the replacement of failed physical components, our engineers can diagnose and resolve issues faster than if we were standing right there in the data center. Additionally, all data center facilities are staffed by qualified data center engineers 24/7/365 (including holidays) to quickly install or replace equipment or cabling.
Power, temperature, humidity, component/service health, and performance metrics are collected across our entire infrastructure every few minutes and aggregated into a single global dashboard monitored by our team. Our years of performance introspection and fine-tuning allow us to provide cloud services with unparalleled levels of performance, reliability, and availability.